Securing Your Network in the Wi-Fi Era
Introduction
Before we had Wi-Fi (local wireless networking for computers and mobile devices), the only way anyone could get in to your network from outside the office was through the Internet. The methods of defending against these attacks are now quite mature. But Wi-Fi opens new attack vectors that require new ways of protecting your systems.
Attacks from the Internet
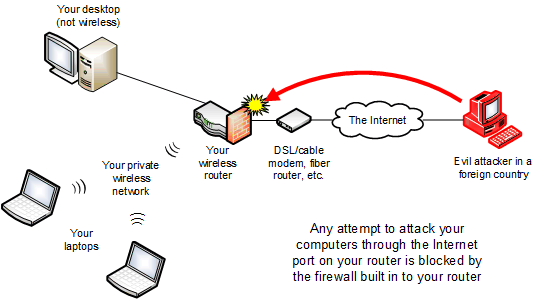
Thousands of people around the world are trying right now to penetrate any network they can find on the Internet, including yours. Seriously, just look at the log files for your firewall or Internet-facing servers, and you'll see failed entry attempts from China and Russia all day and night. Also, criminals run networks that send out billions of junk (spam) e-mails every day, many of which attach programs that will trick your computer into sending them your files and passwords.
Both of these kinds of attacks are easy enough to thwart. Criminals simply can't get past your firewall, and you don't open spam (right?), so your computers and devices are quite secure from the random attacker on the Internet.
Attacks through Wi-Fi
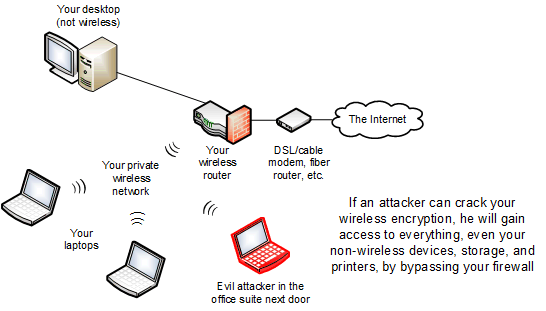
Your Wi-Fi router or access points send signals out on the air in all directions, and anyone near your office can communicate with your wireless infrastructure. Of course, the wireless signal is encrypted with a passphrase, but it is possible to crack Wi-Fi encryption, and how easy it is depends on the age of your equipment and the expertise of those who installed it. And, apart from someone trying to brute-force his way through your encryption, it's even more common for someone who is not authorized to find out what your encryption passphrase is, by seeing it on a sticky note while walking through your office, for example.
Either way, once someone has credentials to access to your signal, in many situations, they can access everything inside your network! You could have an impenetrable firewall, keep all your software up-to-date to prevent security flaws, and have trained users never to open junk mail or download malware, and the attacker can still probe each of your computers, devices, and storage systems directly. Then, with a little more work, he may be able to read company e-mail, and copy or delete databases and files.
Of course, such an attacker needs to be in your proximity. This means, compared to Internet-based attacks, an attack on your network via your wireless signal is more likely to come from someone specifically targeting you. But, even if you don't think anyone would do that, it's still a good idea to secure your system, just like you lock the front door of your house even if nobody has ever tried to open it.
Rogue Access Points
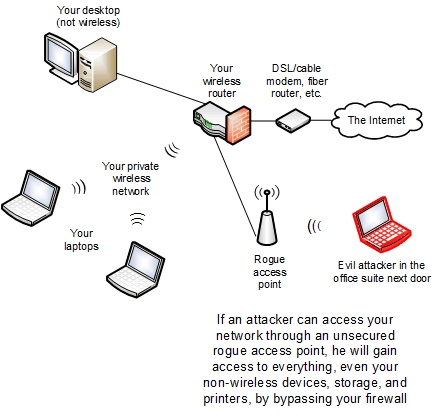
Sometimes, the threat to your network comes from your own employees, often unintentionally. It's quite common for an employee to purchase an inexpensive Wi-Fi access point and plug it in to your wired network without authorization from your IT manager, then share the encryption password with others, or configure no encryption at all or some other form of easy access.
An employee may do this if the performance of your company's Wi-Fi infrastructure is poor in the area where the employee works. Or, he may have brought something like a Sonos speaker system from home (which streams music from the Internet via Wi-Fi), found he couldn't connect it to your company's wireless access points due to your security configuration, and solved the problem by adding his own access point to use the company's Internet connection.
What You Can Do
Consider these tips to secure your network in the Wi-Fi era:
- If your company uses Wi-Fi only for your employees to access the Internet on their personal devices, put your wireless access points outside your firewall. That way, if someone breaks in to your wireless network, they will have no better access to your servers and computers than someone trying to get in remotely over the Internet.
- Configure your wireless access points to require digital certificates for connecting, rather than a shared password, to make it nearly impossible for unauthorized devices to connect.
- Invest in enterprise-grade equipment that is self-monitoring, and can detect, prevent, and report intrusions and rogue access points.
- If you use Wi-Fi for business applications (such as tracking inventory using mobile tablets) and for employees' personal use, set up two wireless networks, one inside the firewall, and one outside. For the one inside, configure high security functions (such as in items 2 or 3 above), and use that for business. Use the one outside for employees' Internet access.
- Invest in professional services to upgrade your Wi-Fi, both to gain the latest technology in security and performance, and to ensure a proper survey is done, so that access points are placed to ensure all areas receive adequate coverage.
- Establish policies, procedures, guidelines, and training to ensure users are aware of and follow rules for sharing passwords or setting up unauthorized equipment.
Some of these tips are easier said than done, and all of them require evaluation within the context of your current network setup and operational needs, so it's best if you consult an IT professional, such as J.D. Fox Micro, for help.